All Checkpoint portals are configured under the Gateway properties.
The IP address of the portal must be that of an IP of an interface on the checkpoint (loopback or physical).
Can either use a different IP for each portal or the same IP for all portals. All portals with the same IP address use the same certificate.
Table Of Contents
There are a few caveats around which certificates are used for which portals:
- If the domain name of a portal URL is unreachable it will use the Mobile Access portal (SSLVPN) certificate
- If the portal for a feature has been configured but the feature itself is not configured correctly it will use the Mobile Access portal certificate
- If the Mobile Access portal certificate has been added but mobile access is disabled it will still use that certificate when Endpoint Connect VPN clients connect
To unassociate a certificate from a portal change the URL of the portal and click on a different submenu. Now you can put back the original URL and no certificate will be associated.
The same certificate can be used for all portals or a selection of portals. You only have to put the certificate on one portal, it will be automatically updated on all others with the same URL or IP.
You can’t use an IP that is not on the checkpoint for a portal, it will let you do it but won’t bind the certificate to the interface.
A loopback interface can be used for the portals, however only one loopback is available on gateway and it cant be in any subnets already assigned to a gateway interface.
add interface lo loopbackip/mask delete interface lo loopbackip
If changing portal addresses is best to change all the addresses, then once done assign the cert and will be assigned to all.This is a useful from Checkpoint on troubleshooting the portals.
The details in this post show the different portal types all using a separate checkpoint interface with a DNS A record and certificate to match.
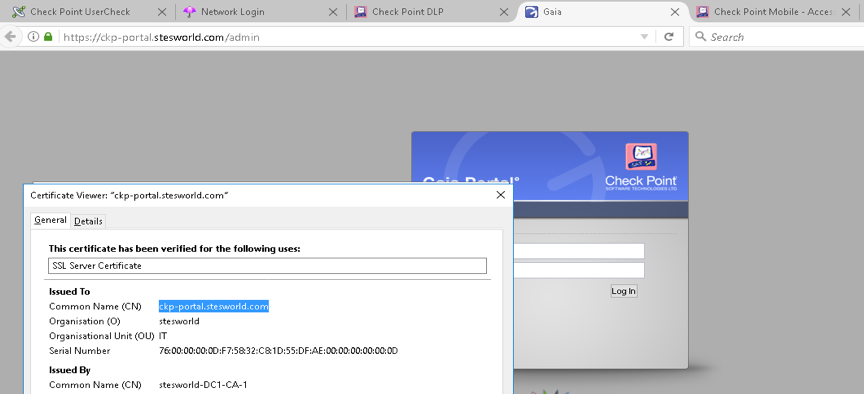
Platform Portal
Eth2.60 10.10.60.4 ckp-portal.stesworld.com/admin
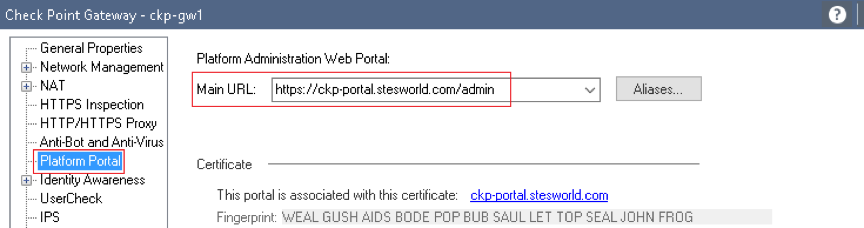
This is the Gaia admin page, can add different port number if want manage on a port other than 443.
Identity Awareness
Eth2.64 10.10.64.4 ckp-connect.stesworld.com/connect
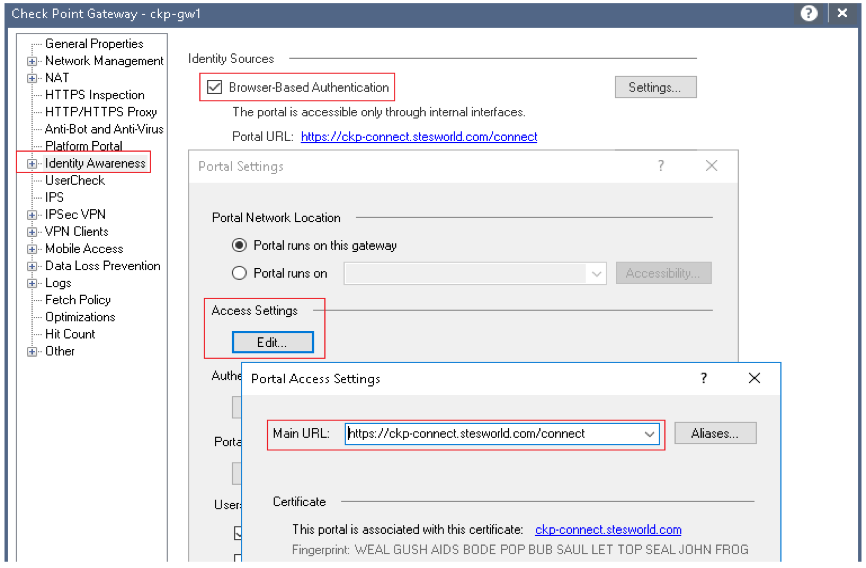
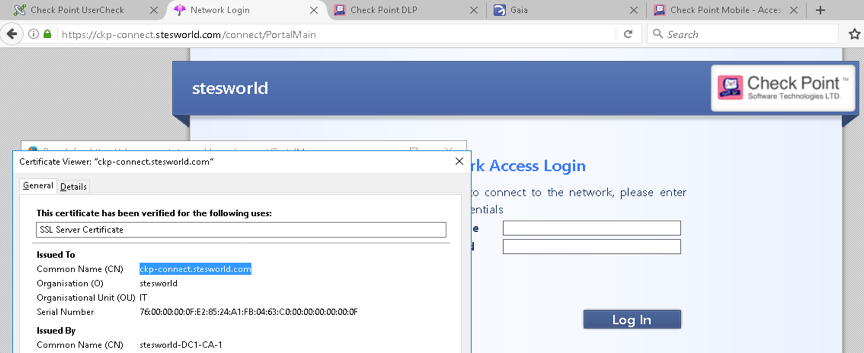
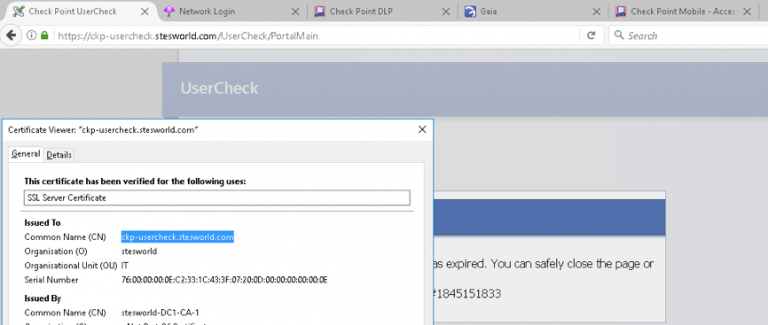
Usercheck
Eth2.61 10.10.61.4 ckp-usercheck.stesworld.com/Usercheck
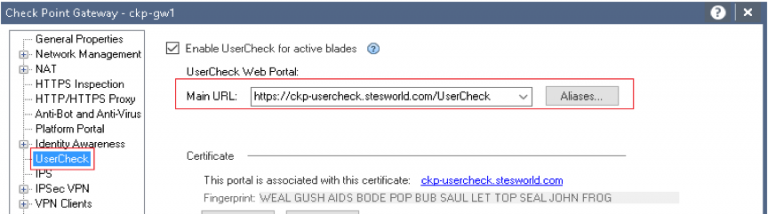
Had to change the URL from the default of http to https to get to work as usercheck will always redirect to HTTPS, so it was redirecting and using the SSLVPN cert.
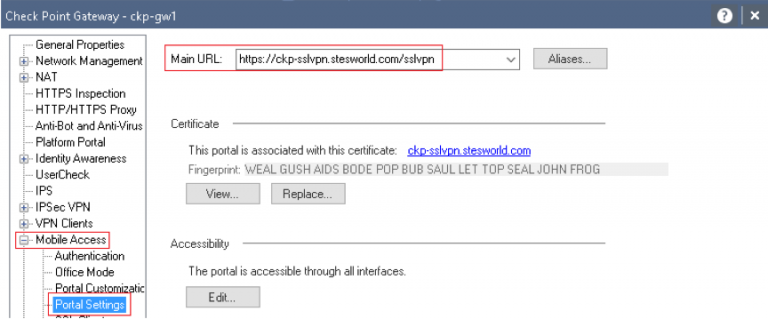
Mobile Access
Eth2.62 10.10.62.4 ckp-sslvpn.stesworld.com.sslvpn
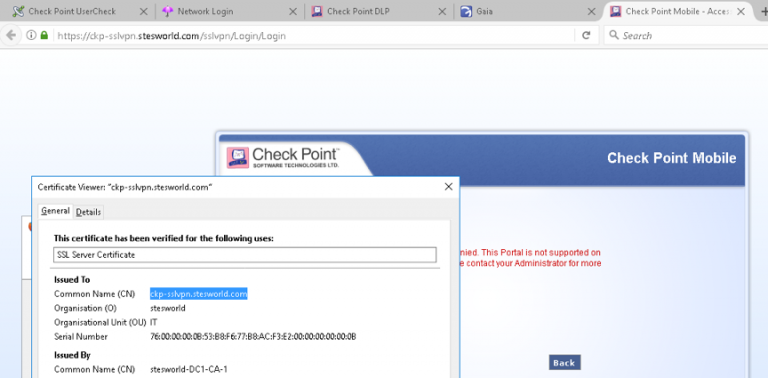
This certificate and page is used by any portal that is misconfigured.
Data Loss Prevention
Eth2.63 10.10.63.4 ckp-dlp.stesworld.com/dlp
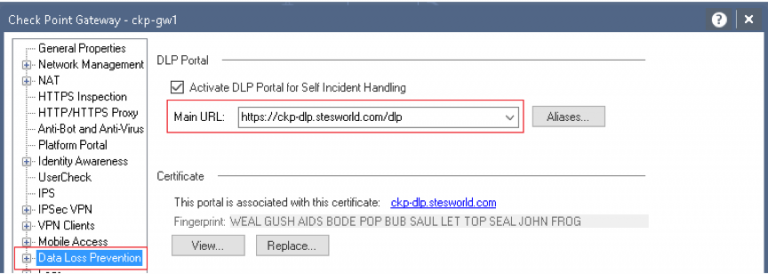
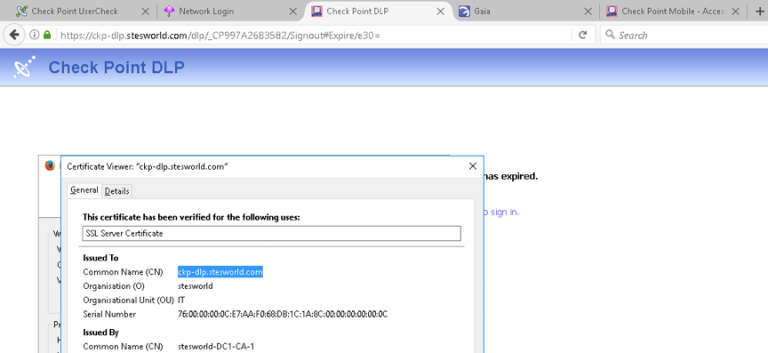
Will only show this portal if the computer/ user is within the organization in the DLP policy. If it isn’t will redirect to either Mobile access or GAIA Portal.
IPsec VPN
Eth0 192.168.1.4 vpn.stesworld.com
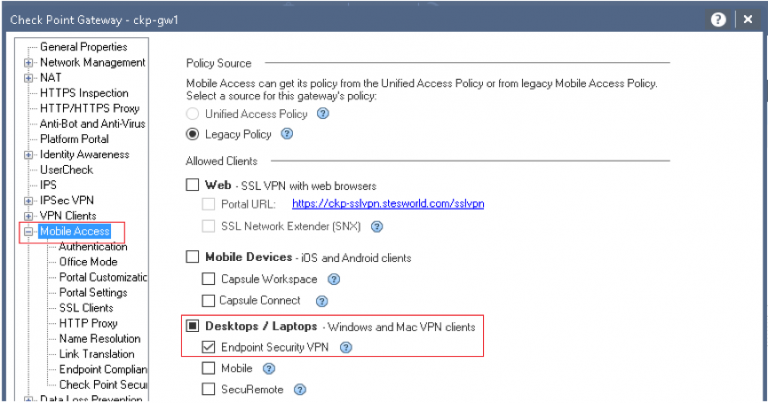
Uses the SSLVPN cert for the Initial Endpoint security VPN connection because Mobile Access » Desktops/ Laptops is enabled for the Endpoint security VPN. Endpoint Connect client, by default, will use port 443 to negotiate the tunnel, even if Visitor Mode is not selected as it uses IKE over TCP for IKE negotiation during phase I. The images show 192.168.255.2 as 192.168.1.4 is NATed to that upstream.
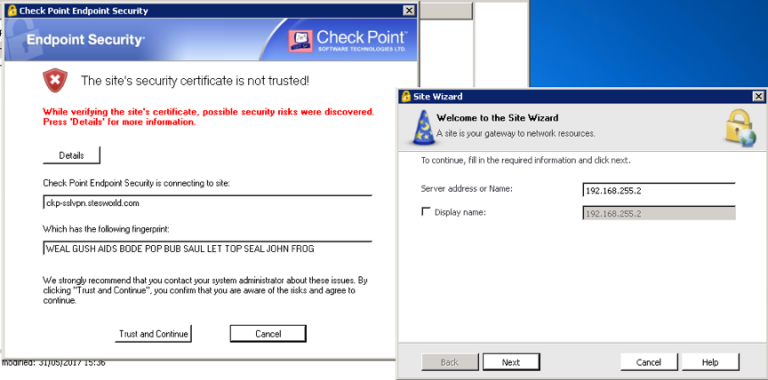
If the certificate is removed from the Mobile Access blade it uses name of the certificate under the IPSEC VPN but the Internal CAs certificate. If you disable the mobile access blade it used the connect name/ certificate, then DLP cert and so on.
The certificate under the IPSEC VPN section is only used if you want to authenticate VPN users (like xauth) using certificates, it isn’t used during the initial VPN connection to verify the gateway.